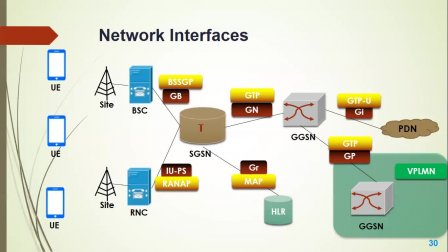
SkillShare – PS Packet Switching Mobile Core Telecom in 2G GSM 3G UMTS and 4G LTE-SkilledHares
English | Size: 1.42 GB
Category: Networks
Learn Basics & Essentials of Packet Core Networks in Telecom Field ( PS Packet Switching in 2G GSM, 3G UMTS & 4G LTE Networks )